Bro Network Security Monitor Training

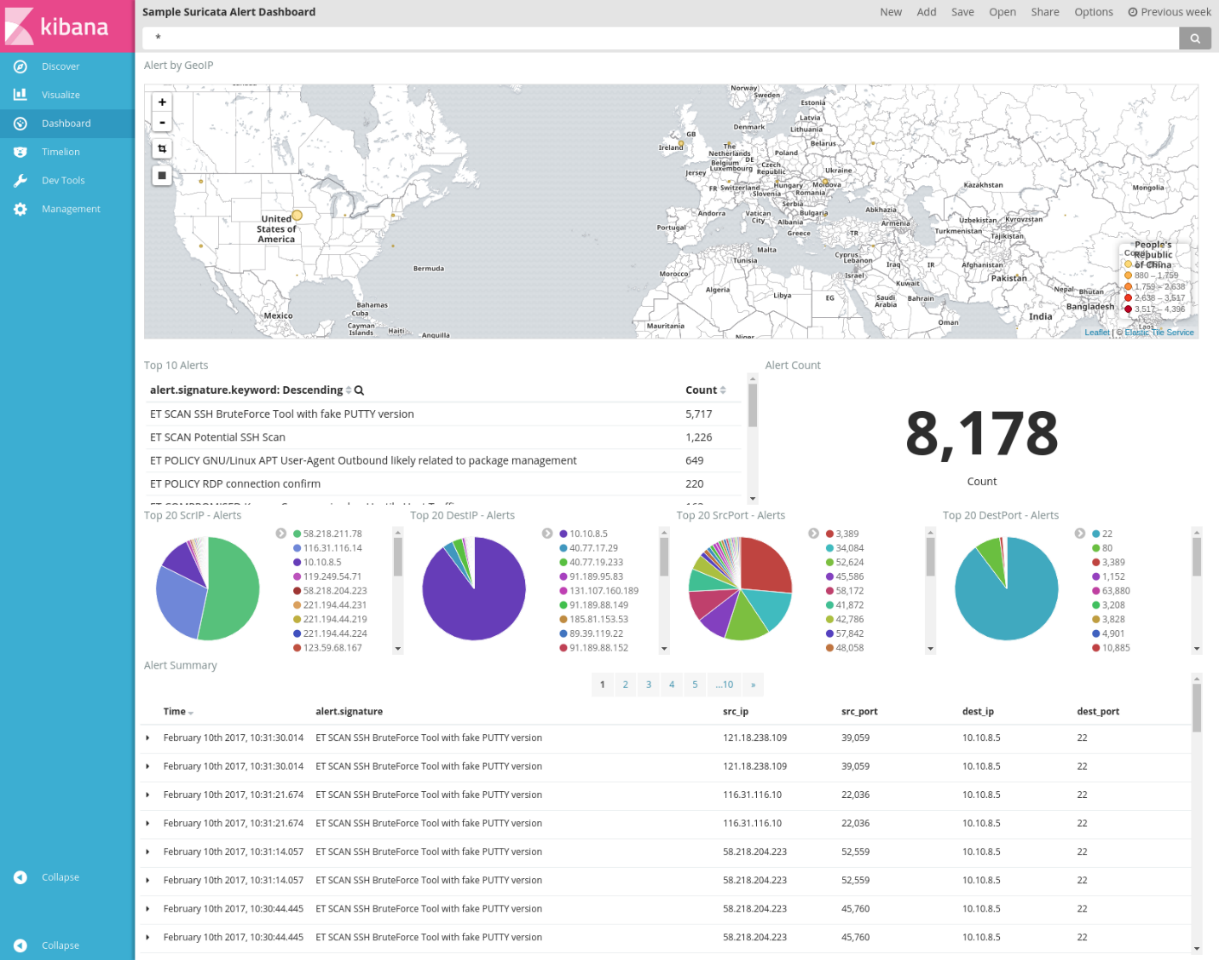
It s based on ubuntu and contains snort suricata bro sguil squert elsa xplico networkminer and many other security tools.
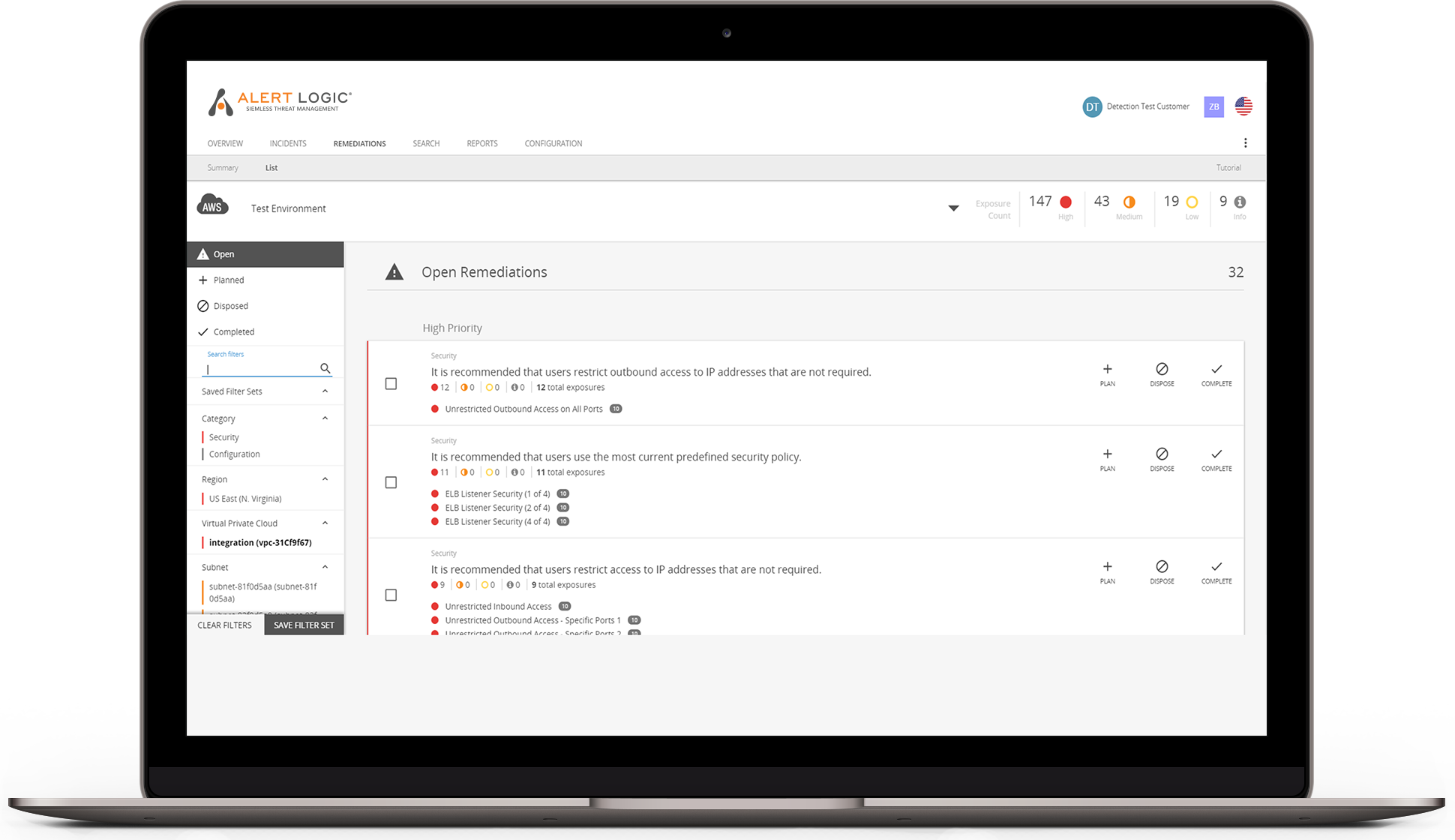
Bro network security monitor training. The easy to use setup wizard allows you to build an army of distributed sensors for your enterprise in minutes. While focusing on network security monitoring bro provides a comprehensive platform for more general network traffic analysis as well. Bro reduces incoming packet streams into higher level events and applies customizable scripts to determine the necessary course of. An open source network security monitoring tool zeek formerly bro is the world s leading platform for network security monitoring.
Bro is a powerful network analysis framework that is much different from the typical ids you may know. Zeek formerly bro is a free and open source software network analysis framework. Overview 2 introduction to bro. Flexible open source and powered by defenders.
This is an introductory workshop you probably won t hear see new things if you have. Security onion is a linux distro for ids intrusion detection and nsm network security monitoring. It is released under the bsd license. Bro events and logs.